Cyber Threat Intelligence: Transforming Data into Defense
Cyber Threat Intelligence (CTI) is not just raw data; it is evidence-based, contextualized knowledge about adversaries, including their motivations, capabilities, and infrastructure. CTI provides the critical context necessary to transform disparate data points into actionable insights, empowering organizations to make proactive, informed decisions about their defense and to anticipate future attacks rather than merely reacting to them. In today's rapidly evolving cyber landscape, where threats are increasingly sophisticated and persistent, CTI serves as the cornerstone of a robust cybersecurity strategy, enabling organizations to move from a reactive stance to a predictive and preventive one.
At Code 0, our CTI services provide a decisive advantage, delivering tailored intelligence that is relevant to your industry, assets, and unique risk profile. We adhere to strict international and European regulations like GDPR and the NIS 2 Directive, ensuring that our intelligence operations are not only effective but also fully compliant and ethically sound. Our deep understanding of the threat landscape, combined with advanced analytical techniques, allows us to provide a predictive edge against the most sophisticated cyber threats. We transform raw data into strategic, operational, and tactical intelligence, empowering your security teams to anticipate, detect, and respond to threats with unparalleled efficiency.
The Pyramid of Pain: A Defender's Guide to Disruption

The Pyramid of Pain is a foundational concept in Cyber Threat Intelligence (CTI) that illustrates the most effective ways to disrupt an adversary. It categorizes Indicators of Compromise (IoCs) by their difficulty for an attacker to change. The higher a defender can operate on the pyramid, the more "pain" they inflict on the attacker, forcing them to expend more resources, time, and effort to adapt their methods and tools. This framework guides our intelligence efforts, prioritizing the collection and analysis of higher-fidelity indicators that yield greater defensive impact.
- Hash Values: At the base of the pyramid, hash values (e.g., MD5, SHA256) represent specific files or malware samples. These are trivial for an attacker to change; even a single byte modification results in a new hash. Blocking based solely on hashes is a low-impact defensive measure, as attackers can easily recompile or repack their tools.
- IP Addresses: Next are IP addresses, which attackers use for command and control (C2) infrastructure or initial access. While slightly more costly to change than hashes, attackers can readily switch IP addresses by using new virtual private servers (VPS), compromised hosts, or different proxy networks.
- Domain Names: Domain names are more persistent than IP addresses but still relatively easy to change. Attackers can register new domains or use domain generation algorithms (DGAs) to rapidly cycle through new C2 domains. However, registering and setting up new domains incurs a higher cost and time investment than simply changing an IP.
- Network/Host Artifacts: This level includes artifacts left on a network or host, such as registry keys, file paths, mutexes, or specific network traffic patterns. These are harder for attackers to change as they often relate to the functionality of their tools or their operational procedures. Modifying these requires changes to their malware or scripts.
- Tools: Moving up, tools refer to the specific software or utilities an attacker uses (e.g., Mimikatz, Cobalt Strike, custom scripts). While attackers can switch tools, it requires them to acquire, develop, or adapt new software, which is a more significant investment of time and resources.
- Tactics, Techniques, and Procedures (TTPs): At the apex are TTPs—the adversary's overall methodology, their unique ways of operating, moving laterally, achieving persistence, or exfiltrating data. These are the most difficult for an attacker to change, as they represent their learned behaviors, skills, and operational tradecraft. Forcing an adversary to alter their TTPs significantly increases their operational cost and risk of detection.
Blocking a file hash (e.g., of a specific malware sample) is trivial for an attacker to bypass—they simply recompile their malware or use a different variant. Similarly, changing IP addresses or domain names is relatively easy. However, forcing an attacker to change their fundamental Tactics, Techniques, and Procedures (TTPs)—like their specific method for lateral movement, privilege escalation, or command and control—requires significant effort and investment on their part, thereby significantly disrupting their operations and increasing the cost of their attack. Our CTI focuses on understanding and countering these higher-level TTPs.
Types of Cyber Threat Intelligence: Tailoring Insights for Impact

CTI is not monolithic; it exists at different levels, each serving a distinct purpose and audience. Understanding these types is crucial for effectively consuming and producing intelligence, ensuring that the right information reaches the right stakeholders at the right time.
Strategic Intelligence: This is high-level, long-term analysis primarily for executives and decision-makers. It answers "Why?"—focusing on adversary motivations, geopolitical trends, the overall cyber threat landscape, and the potential impact on the organization's risk profile and business strategy. It helps in making informed decisions about security investments and strategic direction, guiding long-term defensive postures and resource allocation. For example, a strategic intelligence report might analyze the rise of state-sponsored ransomware groups and their potential impact on critical infrastructure sectors, informing a company's decision to invest in advanced endpoint detection and response (EDR) solutions.
Operational Intelligence: This level of intelligence is for security managers and incident responders. It answers "How?"—detailing the specific methods, tools, and campaigns used by threat actors. This is where MITRE ATT&CK mapping is crucial, providing a common language to describe adversary Tactics, Techniques, and Procedures (TTPs). Operational intelligence helps in understanding how attacks are conducted, enabling the development of effective defensive playbooks and enhancing incident response capabilities. An example would be intelligence on a specific phishing campaign, detailing the email lures, attachment types, and the command-and-control (C2) infrastructure used, allowing a security operations center (SOC) to proactively block malicious domains and train employees on new phishing tactics.
Tactical Intelligence: This is granular, short-term information for frontline analysts and security tools. It answers "What?"—providing Indicators of Compromise (IoCs) like IP addresses, domain names, file hashes, and specific malware signatures. Tactical intelligence can be directly fed into security tools (SIEM, EDR, firewalls, IDS/IPS) for automated blocking and detection, providing immediate, actionable defense mechanisms. For instance, a tactical intelligence feed might provide a list of newly identified malicious IP addresses associated with a botnet, which can be immediately added to firewall blacklists to prevent communication with infected internal hosts.
Consuming & Producing Intelligence: Platforms, APIs, and OSINT

Effective CTI programs require both consuming external intelligence from a variety of sources and generating internal intelligence based on an organization's unique telemetry. This involves leveraging specialized platforms for sharing and analysis, integrating with various APIs, and conducting thorough Open-Source Intelligence (OSINT) gathering.
MISP: The Collaborative Sharing Platform
The Malware Information Sharing Platform (MISP) is a critical open-source tool for CTI. It serves as a platform for sharing, storing, and correlating Indicators of Compromise (IoCs) and threat intelligence. Organizations can subscribe to threat feeds from trusted partners, security communities, and national CERTs, automatically ingesting IoCs and correlating them with internal security events. This collaborative approach ensures that a detection in one organization can quickly become a defense for all others, fostering a collective defense against cyber threats. MISP's robust API allows for seamless integration with existing security tools and workflows. Beyond just IoCs, MISP allows for the sharing of rich contextual information, including adversary profiles, attack campaigns, and detailed event data, making it a powerful tool for structured threat intelligence exchange. Its flexible data model supports various intelligence formats, and its tagging system enables granular categorization and filtering of information.
YARA: The "Grep" for Malware
YARA is a powerful, open-source tool designed to help malware researchers and security analysts identify and classify malware samples. It uses rules based on textual or binary patterns to find strings, hashes, or other features within a file or memory. YARA rules are highly flexible and can be used to detect specific malware families, identify common attacker tools, or even flag suspicious behaviors. Our experts develop custom YARA rules tailored to emerging threats and specific adversary TTPs relevant to your organization. YARA rules are essentially a pattern-matching language, allowing for the creation of signatures that can identify malware based on unique characteristics, such as specific byte sequences, strings, or PE file imports. This makes YARA an invaluable tool for both proactive threat hunting and reactive incident response, enabling rapid identification of malicious artifacts across large datasets.
rule Suspicious_CobaltStrike_Payload
{
meta:
author = "Code 0 CTI Team"
description = "Detects common strings and characteristics in Cobalt Strike beacons"
date = "2025-07-21"
reference = "T1059" // MITRE ATT&CK ID for Command and Scripting Interpreter
strings:
// Common HTTP verbs and paths used in C2 communications
$http_get = "GET /%s HTTP/1.1" wide ascii
$http_post = "POST /%s HTTP/1.1" wide ascii
// Default named pipe used for inter-process communication
$pipe_name = "\\\\.\\pipe\\msagent_"
condition:
// File must be a Windows Portable Executable (PE) file
(uint16(0) == 0x5a4d) and
// Condition: The file is a PE file and contains at least 2 of the specified strings
2 of ($http_get, $http_post, $pipe_name)
}
Beyond structured feeds, Open-Source Intelligence (OSINT) plays a vital role in CTI. Our analysts are adept at leveraging publicly available information from social media, forums, news articles, technical blogs, public code repositories, and even satellite imagery to gather insights into adversary activities, new attack vectors, and emerging threats. This human-driven analysis complements automated feeds, providing a richer, more nuanced understanding of the threat landscape. OSINT is particularly valuable for understanding adversary motivations, identifying their infrastructure, and tracking their movements across the internet, often revealing information that automated tools might miss.
Read More:
Advanced Data Sources and APIs: Fueling Comprehensive CTI
Beyond traditional threat feeds and OSINT, effective CTI relies on integrating diverse and often specialized data sources through robust APIs. This allows for real-time correlation, deeper analysis, and the ability to pivot quickly between different data points to build a holistic threat picture. Our approach leverages a combination of public, private, and proprietary data sources to provide a truly comprehensive view of the threat landscape.
- VirusTotal API: Integrates with VirusTotal to query file hashes, IP addresses, and domain names for known malware, malicious indicators, and community-contributed intelligence. This provides immediate context on suspicious artifacts, allowing our analysts to quickly ascertain the reputation and potential threat level of observed indicators. For example, we can automatically submit a suspicious file hash from an endpoint detection system and receive a report on its known maliciousness, associated campaigns, and behavioral analysis from a vast array of antivirus engines.
- Shodan API: Leverages Shodan to discover internet-connected devices, open ports, and vulnerabilities. This is crucial for understanding an adversary's potential attack surface and identifying exposed infrastructure. We use Shodan to identify misconfigured services, vulnerable versions of software, and open ports that could be exploited by threat actors, providing a proactive view of potential attack vectors. For instance, we can search for specific industrial control systems (ICS) exposed to the internet or identify all web servers running outdated software versions within a target's infrastructure.
- PassiveTotal (RiskIQ) API: Provides historical and current passive DNS, WHOIS, SSL certificate, and other infrastructure data. This helps in mapping adversary infrastructure, identifying related domains, and tracking changes over time. By analyzing historical DNS records, we can uncover previously unknown attacker infrastructure, identify patterns in their domain registration, and link seemingly disparate malicious activities to a common threat actor. This is invaluable for long-term tracking and attribution.
- MISP API: Facilitates automated ingestion and export of threat intelligence from and to MISP instances, enabling seamless sharing and collaboration within trusted communities. Our systems are configured to automatically pull new indicators and events from relevant MISP communities, enriching our internal intelligence and ensuring we are always up-to-date with the latest threats. We also contribute our own anonymized findings back to these communities, fostering collective defense.
- OpenCTI API: Allows for programmatic interaction with OpenCTI platforms, enabling automated enrichment of threat intelligence, creation of new observables, and linking of disparate entities within a knowledge graph. OpenCTI serves as our central repository for structured threat intelligence, allowing us to build rich, interconnected profiles of threat actors, malware, and campaigns. Its API enables automated data ingestion from various sources and facilitates complex queries to uncover hidden relationships.
- Custom Data Lakes: We assist in building and integrating with internal data lakes that aggregate security logs, network flow data, endpoint telemetry, and business context. This proprietary data, combined with external intelligence, provides unparalleled insights into an organization's unique threat landscape. By correlating internal security events with external threat intelligence, we can detect advanced persistent threats (APTs) that might otherwise go unnoticed, and provide highly tailored defensive recommendations.
Forensic Intelligence: Uncovering the Digital Footprints

Forensic intelligence is a critical component of CTI, focusing on the post-incident analysis of digital artifacts to understand the adversary's actions, tools, and techniques. By meticulously examining compromised systems, network traffic, and memory dumps, we can extract valuable indicators that feed back into our threat intelligence platforms, enhancing future detection and prevention capabilities. This deep dive into the remnants of an attack allows us to not only understand *what* happened but also *how* it happened, providing crucial insights for improving defensive postures and developing more resilient systems.
This process often involves a combination of specialized techniques and tools:
- Malware Analysis: Dissecting malicious code (static and dynamic analysis) to understand its functionality, command and control mechanisms, persistence methods, and evasion techniques. This includes reverse engineering binaries and analyzing their behavior in a controlled environment.
- Memory Forensics: Analyzing RAM dumps to identify running processes, network connections, loaded modules, and hidden artifacts that may indicate compromise. Tools like Volatility Framework are essential for extracting volatile data that might be lost upon system shutdown.
- Disk Forensics: Examining hard drive images for evidence of intrusion, data exfiltration, and persistence mechanisms. This involves recovering deleted files, analyzing file system metadata, and identifying suspicious file creations or modifications.
- Network Forensics: Capturing and analyzing network traffic (PCAPs) to reconstruct attack timelines, identify malicious communications, and extract indicators of compromise. This can reveal lateral movement, data exfiltration channels, and communication with command-and-control servers.
- Log Analysis: In-depth review of system, application, and security logs to identify anomalies, suspicious activities, and traces left by attackers. This often involves correlating logs from various sources to build a comprehensive timeline of events.
Integrating External Threat Intelligence: APIs and Platforms
Beyond the foundational concepts of CTI, practical implementation heavily relies on integrating data from various external sources. This often involves leveraging APIs from specialized threat intelligence platforms and open-source tools to enrich internal data, automate analysis, and enhance detection capabilities. Here, we highlight some key platforms and how their data can be integrated, often complementing YARA rules for more effective threat hunting.
VirusTotal: A Crowdsourced Malware Intelligence Platform
VirusTotal aggregates results from numerous antivirus engines, blacklisting services, and data analysis tools to provide comprehensive reports on suspicious files, URLs, domains, and IP addresses. Its API allows for automated submission and retrieval of analysis reports, making it invaluable for quick reputation checks.
import requests
API_KEY = "YOUR_VIRUSTOTAL_API_KEY"
resource = "99017f6eebf4758524a2315d95597506" # Example: MD5 hash of a known malware
url = f"https://www.virustotal.com/api/v3/files/{resource}"
headers = {
"x-apikey": API_KEY
}
response = requests.get(url, headers=headers)
if response.status_code == 200:
data = response.json()
print(data["data"]["attributes"]["last_analysis_stats"])
else:
print(f"Error: {response.status_code} - {response.text}")
Integration with YARA: VirusTotal reports often contain strings or behavioral indicators that can be directly translated into YARA rules. For instance, if a malware sample consistently communicates with a specific C2 domain, a YARA rule can be crafted to detect that domain in network traffic or memory dumps.
AlienVault OTX (Open Threat Exchange): Community-Powered Intelligence
OTX is a free, community-driven threat intelligence platform that allows users to share, research, and consume threat data. It provides a global view of malicious activity, including IP addresses, domains, file hashes, and vulnerabilities. Its API enables automated access to pulses (collections of IoCs) and individual indicators.
import requests
API_KEY = "YOUR_OTX_API_KEY"
indicator = "8.8.8.8" # Example: Google DNS IP
url = f"https://otx.alienvault.com/api/v1/indicators/IPv4/{indicator}/general"
headers = {
"X-OTX-API-KEY": API_KEY
}
response = requests.get(url, headers=headers)
if response.status_code == 200:
data = response.json()
print(data["indicator"])
else:
print(f"Error: {response.status_code} - {response.text}")
Integration with YARA: IoCs from OTX pulses, such as specific malware hashes or C2 domains, can be directly incorporated into YARA rules for network or endpoint detection. OTX also provides context that can help refine YARA rules, making them more precise and reducing false positives.
AbuseIPDB: Reporting and Checking Malicious IPs
AbuseIPDB is a database for reporting and checking IP addresses that have been associated with malicious activity. It helps network administrators and security professionals identify and block attackers. Its API allows for checking an IP's reputation and submitting new reports.
import requests
API_KEY = "YOUR_ABUSEIPDB_API_KEY"
ip_address = "1.1.1.1" # Example: Cloudflare DNS
url = "https://api.abuseipdb.com/api/v2/check"
headers = {
"Accept": "application/json",
"Key": API_KEY
}
params = {
"ipAddress": ip_address,
"maxAgeInDays": "90"
}
response = requests.get(url, headers=headers, params=params)
if response.status_code == 200:
data = response.json()
print(data["data"]["abuseConfidenceScore"])
else:
print(f"Error: {response.status_code} - {response.text}")
Integration with YARA: While AbuseIPDB primarily deals with IP reputation, the context provided in reports (e.g., type of attack, associated malware) can inform the development of YARA rules. For example, if an IP is reported for distributing a specific type of malware, YARA rules can be created to detect that malware on endpoints.
Talos Intelligence: Cisco's Threat Research

Cisco Talos is one of the largest commercial threat intelligence teams in the world, providing comprehensive research on vulnerabilities, malware, and emerging threats. While their full intelligence platform is commercial, they offer public blogs and advisories that are a rich source of information for threat hunters. Their data often includes detailed technical analysis that can be directly used to create YARA rules.
Integration with YARA: Talos advisories frequently include specific IoCs, such as file hashes, network signatures, and behavioral patterns, which are ideal for direct translation into YARA rules. Their detailed reports on malware families often provide the necessary depth to craft highly effective and precise YARA signatures.
Read More:
Most Important Top 10 Threat Intel Websites
- Mandiant (FireEye) Threat Research Blog
- Recorded Future Blog
- CrowdStrike Blog
- Palo Alto Networks Unit 42
- KrebsOnSecurity
- Threatpost
- BleepingComputer
- Schneier on Security
- Dark Reading
- CIS (Center for Internet Security) Blog
Challenges and Best Practices in CTI
While the benefits of CTI are undeniable, its implementation and effective utilization come with a unique set of challenges. Overcoming these requires a strategic approach and adherence to best practices.
- Information Overload: The sheer volume of threat data from various sources can be overwhelming.
Best Practice: Implement automated ingestion and correlation tools (like MISP, OpenCTI) and focus on intelligence relevant to your specific threat landscape and assets. Prioritize high-fidelity indicators and contextualized reports. - Lack of Context: Raw IoCs (hashes, IPs) without context provide limited value.
Best Practice: Always strive for contextualized intelligence. Understand the "who, what, when, where, why, and how" behind an indicator. Leverage frameworks like MITRE ATT&CK to map IoCs to adversary TTPs. - Timeliness and Actionability: Intelligence quickly becomes stale. It must be actionable to be valuable.
Best Practice: Establish clear intelligence requirements and dissemination channels. Ensure intelligence reaches the right stakeholders (analysts, leadership) in a timely and digestible format, enabling rapid decision-making and defensive actions. - Skill Gap: Analyzing and producing high-quality CTI requires specialized skills.
Best Practice: Invest in training for your security teams in areas like malware analysis, digital forensics, OSINT, and intelligence analysis frameworks. Consider partnering with specialized CTI providers. - Integration Challenges: Integrating CTI into existing security tools and workflows can be complex.
Best Practice: Utilize APIs and standardized formats (e.g., STIX/TAXII) for seamless integration between CTI platforms, SIEMs, EDRs, and other security controls. Automate intelligence consumption and action where possible.
Threat Actor Profiles
Understanding the adversary is key to effective defense. Here are profiles of two prominent threat actors, detailing their suspected affiliations, primary targets, common malware, and key Tactics, Techniques, and Procedures (TTPs) mapped to the MITRE ATT&CK Framework. This insight allows organizations to tailor their defenses against specific, real-world threats by understanding who is likely to target them and how. By studying these profiles, defenders can anticipate attack methodologies, prioritize defenses, and develop more effective threat hunting strategies.

APT29 (Cozy Bear)
- Suspected State Affiliation: Russia (SVR)
- Primary Target Sectors: Government, Diplomatic, Think Tanks, Healthcare, Energy
- Commonly Used Malware: Sunburst, WellMail, WellMess, GoldMax
- Key MITRE ATT&CK TTPs:
- T1566 Phishing: Spearphishing campaigns are a primary initial access vector.
- T1588.002 Tool: Acquiring and using legitimate software (like Cobalt Strike) to blend in.
- T1071.001 Application Layer Protocol (HTTP): Extensive use of HTTP/S for C2 communications.
- T1059.003 Command and Scripting Interpreter (PowerShell): Heavy reliance on PowerShell for execution and lateral movement.

Lazarus Group
- Suspected State Affiliation: North Korea
- Primary Target Sectors: Financial (Cryptocurrency), Defense, Entertainment
- Commonly Used Malware: WannaCry, Dacls, VHD Ransomware
- Key MITRE ATT&CK TTPs:
- T1204.002 Malicious File: Using malicious documents and macros for initial compromise.
- T1574.001 Hijack Execution Flow: DLL hijacking to execute malicious code.
- T1486 Data Encrypted for Impact: Deployment of ransomware for financial gain or disruption.
- T1562.001 Impair Defenses (Disable or Modify Tools): Actively attempts to disable security software on compromised hosts.
Related Projects
Threat Hunting & Intel
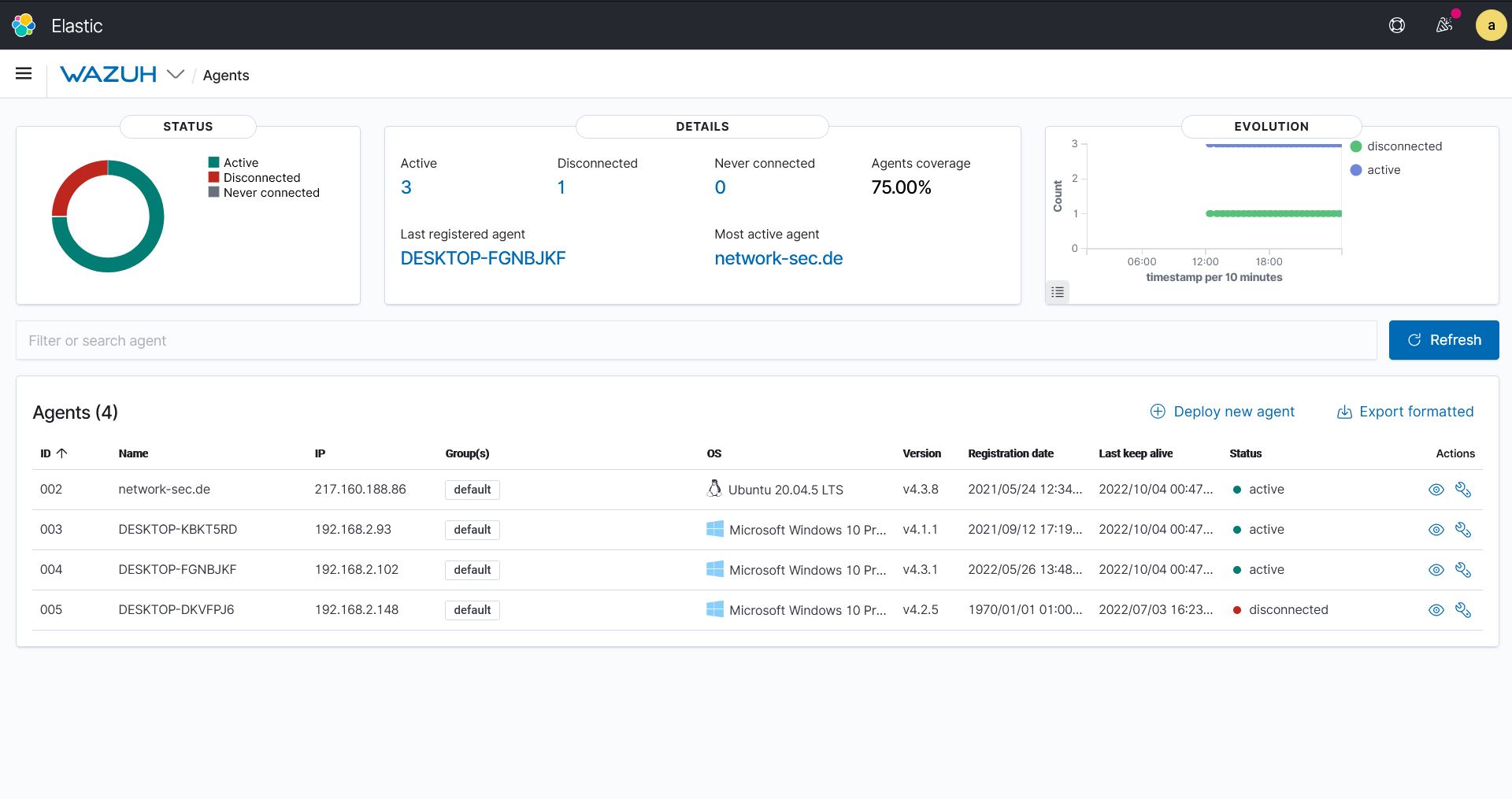
Our threat hunting lab utilizes a diverse stack of SIEM solutions like Wazuh and OpenCTI, alongside online intelligence platforms, to actively surveil our networks and analyze threats in real-time.
OSINT Aggregator
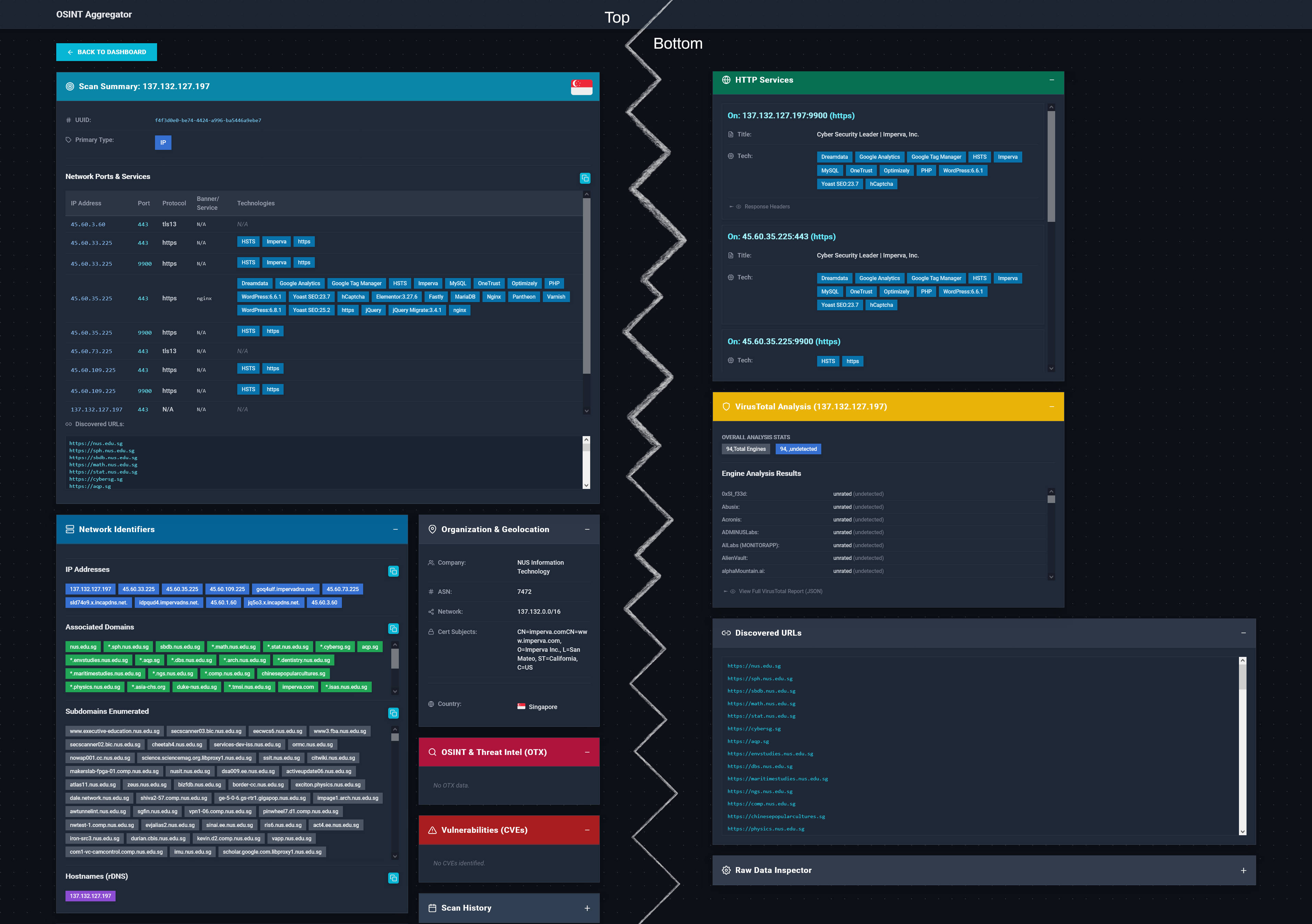
This OSINT Aggregator automates reconnaissance by ingesting data from multiple sources to enumerate targets, identify vulnerabilities, and feed active scanners, featuring a complete-passive mode for stealthy intelligence gathering without direct contact.